SystemMen - How to change SSH port number in CentminMod? By default, Linux servers use port 22 for SSH service. This is a service for you to login and control your server.
And of course, this is known to all hackers. Using that default configuration is not good, is not safe for your server. So you need to change that.
Change SSH port number in CentminMod
Try fast volume bot solana on Orca.

Okay, if you’re a pretty good person using Linux. Changing port for SSH service is quite simple for you. Otherwise, you will block yourself from logging into the server.
So, CentminMod has supported you. In the admin menu, it provides an option that allows you to select another port to run the SSH service.
--------------------------------------------------------
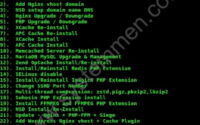
Centmin Mod Menu 123.09beta01 centminmod.com
--------------------------------------------------------
1). Centmin Install
2). Add Nginx vhost domain
3). NSD setup domain name DNS
4). Nginx Upgrade / Downgrade
5). PHP Upgrade / Downgrade
6). XCache Re-install
7). APC Cache Re-install
8). XCache Install
9). APC Cache Install
10). Memcached Server Re-install
11). MariaDB MySQL Upgrade & Management
12). Zend OpCache Install/Re-install
13). Install/Reinstall Redis PHP Extension
14). SELinux disable
15). Install/Reinstall ImagicK PHP Extension
16). Change SSHD Port Number
17). Multi-thread compression: zstd,pigz,pbzip2,lbzip2
18). Suhosin PHP Extension install
19). Install FFMPEG and FFMPEG PHP Extension
20). NSD Install/Re-Install
21). Update - Nginx + PHP-FPM + Siege
22). Add WordPress Nginx vhost + Cache Plugin
23). Update Centmin Mod Code Base
24). Exit
--------------------------------------------------------
Enter option [ 1 - 24 ] 16
--------------------------------------------------------
Look and select menu number 16.
A piece of information will print to the screen for you, it will tell you what port number you currently use for SSH service.
And you’ll have to choose a certain number <1024 to be the running port for the SSH service.
As in the following paragraph, I chose port 222.
************************************************* * Setup sshd ************************************************* -------------------------- backup sshd_config -------------------------- cp -a /etc/ssh/sshd_config /etc/ssh/sshd_config-backup -------------------------- change ssh port -------------------------- You'll be asked what your current default SSH port is (default = 22 or 22). Then asked which SSH port number you want to change to. New SSH port should be a number below and less than <1024. Your current default SSH port is: 22 or 22 Enter existing SSH port number (default = 22 for fresh installs): 22 Enter the SSH port number you want to change to: 222
And then, CentminMod will automatically do the rest. You just wait about 30 seconds for it to finish your job.
Post 222 configured in /etc/ssh/sshd_config Port 222 iptables -I INPUT -p tcp --dport 22 -j REJECT iptables -I INPUT -p tcp --dport 222 -j ACCEPT systemctl restart iptables.service systemctl restart csf.service Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' Flushing chain `PREROUTING' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `ALLOWDYNIN' Flushing chain `ALLOWDYNOUT' Flushing chain `ALLOWIN' Flushing chain `ALLOWOUT' Flushing chain `DENYIN' Flushing chain `DENYOUT' Flushing chain `INVALID' Flushing chain `INVDROP' Flushing chain `LOCALINPUT' Flushing chain `LOCALOUTPUT' Flushing chain `LOGDROPIN' Flushing chain `LOGDROPOUT' Flushing chain `PORTFLOOD' Flushing chain `UDPFLOOD' Deleting chain `ALLOWDYNIN' Deleting chain `ALLOWDYNOUT' Deleting chain `ALLOWIN' Deleting chain `ALLOWOUT' Deleting chain `DENYIN' Deleting chain `DENYOUT' Deleting chain `INVALID' Deleting chain `INVDROP' Deleting chain `LOCALINPUT' Deleting chain `LOCALOUTPUT' Deleting chain `LOGDROPIN' Deleting chain `LOGDROPOUT' Deleting chain `PORTFLOOD' Deleting chain `UDPFLOOD' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' Flushing chain `PREROUTING' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' csf: FASTSTART loading DROP no logging (IPv4) csf: FASTSTART loading DROP no logging (IPv6) LOG tcp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *TCP_IN Blocked* " LOG tcp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 tcp flags:0x17/0x02 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *TCP_OUT Blocked* " LOG udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *UDP_IN Blocked* " LOG udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *UDP_OUT Blocked* " LOG icmp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *ICMP_IN Blocked* " LOG icmp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *ICMP_OUT Blocked* " LOG tcp opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *TCP6IN Blocked* " LOG tcp opt in * out * ::/0 -> ::/0 tcp flags:0x17/0x02 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *TCP6OUT Blocked* " LOG udp opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *UDP6IN Blocked* " LOG udp opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *UDP6OUT Blocked* " LOG icmpv6 opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *ICMP6IN Blocked* " LOG icmpv6 opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *ICMP6OUT Blocked* " LOG all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *Port Flood* " LOG all opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *Port Flood* " DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 REJECT all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 reject-with icmp-port-unreachable DROP all opt in * out * ::/0 -> ::/0 REJECT all opt in * out * ::/0 -> ::/0 reject-with icmp6-port-unreachable DENYOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 DENYIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ALLOWOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ALLOWIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 DENYOUT all opt in * out !lo ::/0 -> ::/0 DENYIN all opt in !lo out * ::/0 -> ::/0 ALLOWOUT all opt in * out !lo ::/0 -> ::/0 ALLOWIN all opt in !lo out * ::/0 -> ::/0 csf: FASTSTART loading Packet Filter (IPv4) csf: FASTSTART loading Packet Filter (IPv6) DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 INVALID tcp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 INVALID tcp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 DROP all opt in * out * ::/0 -> ::/0 INVALID tcp opt in !lo out * ::/0 -> ::/0 INVALID tcp opt in * out !lo ::/0 -> ::/0 csf: IPSET creating set chain_DENY csf: IPSET creating set chain_6_DENY csf: FASTSTART loading csf.deny (IPv4) csf: FASTSTART loading csf.deny (IPv6) csf: FASTSTART loading csf.deny (IPSET) csf: IPSET creating set chain_ALLOWDYN ACCEPT all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 match-set chain_ALLOWDYN src ACCEPT all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 match-set chain_ALLOWDYN dst csf: IPSET creating set chain_6_ALLOWDYN ACCEPT all opt in * out * ::/0 -> ::/0 match-set chain_6_ALLOWDYN src ACCEPT all opt in * out * ::/0 -> ::/0 match-set chain_6_ALLOWDYN dst ALLOWDYNIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ALLOWDYNOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ALLOWDYNIN all opt in !lo out * ::/0 -> ::/0 ALLOWDYNOUT all opt in * out !lo ::/0 -> ::/0 csf: IPSET creating set chain_ALLOW csf: IPSET creating set chain_6_ALLOW csf: FASTSTART loading csf.allow (IPv4) csf: FASTSTART loading csf.allow (IPv6) csf: FASTSTART loading csf.allow (IPSET) tcp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 tcp dpt:21 state NEW recent: SET name: 21 side: source mask: 255.255.255.255 PORTFLOOD tcp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 tcp dpt:21 state NEW recent: UPDATE seconds: 300 hit_count: 20 name: 21 side: source mask: 255.255.255.255 tcp opt in !lo out * ::/0 -> ::/0 tcp dpt:21 state NEW recent: SET name: 21 side: source mask: ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff PORTFLOOD tcp opt in !lo out * ::/0 -> ::/0 tcp dpt:21 state NEW recent: UPDATE seconds: 300 hit_count: 20 name: 21 side: source mask: ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 DROP all opt in * out * ::/0 -> ::/0 RETURN udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 owner UID match 0 RETURN udp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 100/sec burst 500 LOG all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *UDPFLOOD* " REJECT udp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 reject-with icmp-port-unreachable UDPFLOOD udp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 RETURN udp opt in * out * ::/0 -> ::/0 owner UID match 0 RETURN udp opt in * out !lo ::/0 -> ::/0 limit: avg 100/sec burst 500 LOG all opt in * out * ::/0 -> ::/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *UDPFLOOD* " REJECT udp opt in * out !lo ::/0 -> ::/0 reject-with icmp6-port-unreachable UDPFLOOD udp opt in * out !lo ::/0 -> ::/0 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 limit: avg 1/sec burst 5 LOGDROPIN icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT icmpv6 opt in !lo out * ::/0 -> ::/0 ACCEPT icmpv6 opt in * out !lo ::/0 -> ::/0 ACCEPT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT all opt in !lo out * ::/0 -> ::/0 state RELATED,ESTABLISHED ACCEPT all opt in * out !lo ::/0 -> ::/0 state RELATED,ESTABLISHED csf: FASTSTART loading TCP_IN (IPv4) csf: FASTSTART loading TCP6_IN (IPv6) csf: FASTSTART loading TCP_OUT (IPv4) csf: FASTSTART loading TCP6_OUT (IPv6) csf: FASTSTART loading UDP_IN (IPv4) csf: FASTSTART loading UDP6_IN (IPv6) csf: FASTSTART loading UDP_OUT (IPv4) csf: FASTSTART loading UDP6_OUT (IPv6) ACCEPT all opt -- in lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt -- in * out lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt in lo out * ::/0 -> ::/0 ACCEPT all opt in * out lo ::/0 -> ::/0 LOGDROPOUT all opt in * out !lo ::/0 -> ::/0 LOGDROPIN all opt in !lo out * ::/0 -> ::/0 csf: FASTSTART loading DNS (IPv4) csf: FASTSTART loading DNS (IPv6) LOCALOUTPUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOCALINPUT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 LOCALOUTPUT all opt in * out !lo ::/0 -> ::/0 LOCALINPUT all opt in !lo out * ::/0 -> ::/0 *WARNING* LF_DISTFTP sanity check. LF_DISTFTP = 40. Recommended range: 0-20 (Default: 0) *WARNING* LF_DISTFTP_UNIQ sanity check. LF_DISTFTP_UNIQ = 40. Recommended range: 2-20 (Default: 2) *WARNING* DENY_TEMP_IP_LIMIT sanity check. DENY_TEMP_IP_LIMIT = 2000. Recommended range: 10-1000 (Default: 100) *WARNING* PT_LOAD_LEVEL sanity check. PT_LOAD_LEVEL = 1. Recommended range: 2-20 (Default: 6) *WARNING* RESTRICT_SYSLOG is disabled. See SECURITY WARNING in /etc/csf/csf.conf. ************************************************* * Setup sshd complete ************************************************* To check to see if you can access your server via the new port keep this existing SSH2 connection open, and start a new SSH2 connection to this server connecting via the new SSH2 port if you can connect, then it's working. If you can't connect, using your existing SSH2 logged in connection, edit and check /etc/csf/csf.conf and your iptables /etc/sysconfig/iptables and service iptables status making sure the new port number you specified is correctly set *************************************************
SSH to your server after change port number
If before, to ssh to your server, you just need to type the command as below. For example, your server has a ip address of 192.168.1.10.
ssh root@192.168.1.10
Now, you need to type the following command to be able to login to the server. In the example, I changed to port 222, change number 222 to the number you changed above.
ssh -p 222 root@192.168.1.10
Conclusion
This is just a simple thing but quite useful in protecting your server. Help it avoid brute-force attacks aimed at SSH service.
You need to do this immediately after installing CentminMod. Don’t be subjective, trust me, when you just created vps and made it public, the auto bots scanned your vps (server).
«« How to change non-www to www in CentminModHow to disable Pure-FTPD in CentminMod »»